Table of Contents
In today’s digital age, where data breaches and cyber threats are on the rise, it’s essential to have robust security measures in place. One such security tool is an intrusion detection system (IDS) that can help detect and prevent potential intrusions into your digital systems.
So, what is IDS? In simple terms, it’s a security system designed to monitor network traffic and system activity in real-time, alerting administrators to any suspicious activity. But it’s much more than that. IDS is a tool that forms the backbone of any cybersecurity strategy, playing a vital role in detecting and mitigating potential threats while safeguarding your valuable digital assets.
Key Takeaways
- IDS is a security tool that helps detect and prevent potential intrusions into digital systems
- It monitors network traffic and system activity in real-time
- IDS plays a crucial role in detecting and mitigating potential cybersecurity threats
- It forms the backbone of any cybersecurity strategy
- IDS safeguards valuable digital assets
Understanding IDS: Key Concepts and Functionality
Intrusion Detection Systems (IDS) play a crucial role in detecting and preventing potential security threats in digital infrastructures. In this section, we will explore the key concepts and functionality of IDS to gain a deeper understanding of how they work and what they offer in terms of cybersecurity protection.
How IDS Works
IDS work by monitoring network traffic and identifying any suspicious or unusual activity that may indicate an intrusion attempt. When an anomaly is detected, the IDS triggers an alert to notify security personnel of the potential threat. IDS can operate in two modes: signature-based and anomaly-based detection methods.
“Signature-based detection methods use a database of known attack patterns to identify potential threats, while anomaly-based detection methods learn the normal behaviour patterns and compare them to the current network activity to detect any deviations.”
Components of IDS
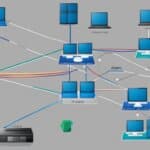
An IDS typically comprises three components: the sensor, console, and central management server. The sensor collects data from the network, the console processes and analyses the information, and the central management server handles the configuration and management of multiple sensors. IDS sensors can be either host-based or network-based, depending on where the data is collected.
Types of IDS
There are several types of IDS systems, including network-based IDS (NIDS), host-based IDS (HIDS), and hybrid IDS (HIDS/NIDS). Regardless of the type, IDS enables organizations to take a proactive approach in securing their digital infrastructures and protecting against potential security threats.
| IDS Type | Description |
|---|---|
| Network-based IDS (NIDS) | Monitors network traffic for security threats, including external attacks and unauthorized access attempts. |
| Host-based IDS (HIDS) | Monitors host devices for unusual activity that may indicate a security breach, such as unauthorized access attempts or changes to system files. |
| Hybrid IDS (HIDS/NIDS) | Combines both network-based and host-based IDS features to enhance overall security protection. |
By comprehending the inner workings of IDS, it is possible to implement a robust cybersecurity strategy that provides comprehensive protection against potential security threats. The next section will outline the numerous benefits of incorporating IDS into your digital environment.
The Benefits of Implementing IDS for Cybersecurity
Implementing intrusion detection systems (IDS) as part of your cybersecurity strategy has numerous advantages. Let’s explore some of the benefits:
- Enhances Security Measures: IDS offers an additional layer of security to your system, detecting possible intrusions before they cause severe damage.
- Provides Real-time Threat Detection: IDS continuously monitors the network, alerting security administrators in real-time about possible attacks.
- Early Identification and Mitigation of Potential Cyber Threats: IDS enables the early identification and mitigation of potential threats, preventing serious consequences.
- Cost-Effective: Implementing IDS can be cost-effective, providing detailed reports that enable security administrators to take the necessary action.
Overall, incorporating IDS into your cybersecurity framework can improve your system’s resilience, giving you peace of mind knowing your digital assets are protected. By implementing IDS, you can monitor, detect and respond to real-time threats, minimizing damage and disruptions to your business.
Conclusion
Intrusion detection systems (IDS) are an essential component of modern-day cybersecurity, providing real-time threat detection and enhancing security measures. By understanding the inner workings of IDS, you can make informed decisions about safeguarding your digital assets from potential cyber threats.
The benefits of implementing IDS are numerous, including early identification and mitigation of potential threats, enhanced security measures, and improved protection of sensitive data. By recognizing the significance of IDS, you can take proactive steps to maintain the integrity of your digital infrastructure.
In conclusion, IDS plays a vital role in detecting and preventing potential cyber threats and is an indispensable tool in today’s digital landscape. Incorporating IDS as part of your cybersecurity strategy is a crucial step in safeguarding your digital environment. Stay vigilant, stay informed, and stay secure.
FAQ
What are intrusion detection systems (IDS)?
Intrusion Detection Systems (IDS) are cybersecurity tools that monitor and analyze network traffic to detect and respond to potential unauthorized access or malicious activities.
How does an IDS work?
An IDS works by monitoring network traffic and comparing it against known patterns or signatures of known threats. It can also utilize behavioral analysis to identify abnormal or suspicious activities. When a potential intrusion is detected, the IDS raises an alert or takes immediate action to block the threat.
What are the components of an IDS?
An IDS typically consists of sensors or agents that collect network data, a central management console for analysis and reporting, and a database to store logs and alerts. Some IDS may also incorporate machine learning algorithms to enhance threat detection capabilities.
What are the different types of IDS?
There are two primary types of IDS: network-based IDS (NIDS) and host-based IDS (HIDS). NIDS monitors network traffic at the network level, while HIDS focuses on monitoring individual hosts or devices for potential intrusions. Some IDS solutions also combine both approaches for comprehensive protection.
What are the benefits of implementing an IDS?
Implementing an IDS provides several advantages for cybersecurity. It enhances security measures by identifying potential threats in real-time, allowing proactive response and mitigation. IDS also aids in the early detection and prevention of attacks, minimizing the risk of data breaches and compromised systems.
Can an IDS prevent all cyber threats?
An IDS serves as an important layer of defense against cyber threats, but it cannot guarantee complete protection. It is essential to combine IDS with other security measures, such as firewalls, antivirus software, and user awareness training, to establish a robust cybersecurity infrastructure.
How often should an IDS be updated?
Regular updating and patching of the IDS software and security signatures are crucial to ensure it can effectively detect and respond to the latest threats. Follow the recommendations and best practices provided by the IDS vendor to maintain an up-to-date and secure intrusion detection system.