Table of Contents
Log4j is a widely used open-source logging framework maintained by Apache. It serves as a logging utility for Java-based applications, allowing developers to record and manage system log messages efficiently. However, recently, Log4j has gained significant attention due to a critical vulnerability that has been discovered.
In December 2021, the Log4j vulnerability was identified as a zero-day flaw, which means that it became known without a security fix or patch readily available. This raised concerns and posed a serious risk to the security of numerous systems and applications.
As an open-source logging framework, Log4j allows applications to communicate with other services on a system, making it an attractive target for attackers looking to exploit its capabilities. The vulnerability enables malicious individuals to inject malicious code into the logs, potentially leading to successful denial-of-service attacks.
This vulnerability has been described as one of the most severe cybersecurity flaws by experts in the industry. Its impact has prompted extensive efforts from cybersecurity professionals to assess and remediate their environments.
Despite the challenges posed by the Log4j vulnerability, it is crucial for organizations to understand its implications and take necessary measures to mitigate the risks. In the following sections, we will delve deeper into what Log4j is, how the exploit works, and the impact it has had on various systems and applications.
What is Log4j and how does the exploit work?
Log4j is an open-source logging framework maintained by Apache, widely used in Java-based systems and applications. It serves as a powerful utility for logging messages and facilitating communication with other services on a system.
The vulnerability in Log4j poses a significant risk to the security of these systems by allowing attackers to inject malicious code into the logs. This code can then be executed on the targeted system, enabling various types of attacks.
The exploit of Log4j was initially discovered in the game Minecraft, where attackers were able to exploit the chat logging feature to execute remote code. This sparked the attention of the cybersecurity community, leading to the development and sharing of Proof of Concept (POC) code on platforms like GitHub.
A specific POC for Log4j leveraged the Java Naming and Directory Interface (JNDI) functionality to redirect the server to a fake Lightweight Directory Access Protocol (LDAP) server controlled by the attacker. This redirect gives the attacker complete control over the targeted system, enabling the execution of malware and the potential exfiltration of sensitive information.
The crafted payload in the Log4j exploit takes advantage of the framework’s ability to communicate with external services. By injecting malicious code into the logs, attackers can manipulate the communication process and gain unauthorized control over the remote system.
This vulnerability highlights the importance of securely implementing and maintaining open-source frameworks like Log4j. Constant vigilance and prompt patching are necessary to protect against potential exploits and maintain a secure software environment.
Example Log4j Exploit Process:
| Step | Description |
|---|---|
| 1 | Attacker identifies a target system running Log4j. |
| 2 | The attacker crafts a payload containing malicious code. |
| 3 | The attacker injects the payload into the logs of the targeted system. |
| 4 | Log4j processes the logs and executes the injected code. |
| 5 | The attacker gains remote control of the system. |
| 6 | Malware is executed on the compromised system, allowing for further exploitation and potential exfiltration of sensitive information. |
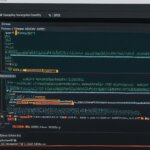
The above image represents the Log4j exploit process, demonstrating how attackers can exploit the vulnerability to gain control of a remote system and execute malicious actions.
Impact and Mitigation of the Log4j Exploit
The Log4j vulnerability has had a significant impact on systems worldwide, leading to a multitude of exploit attempts and successful denial-of-service attacks. Various software applications, including renowned platforms such as Apache Struts, Apache Solr, Apple iCloud services, Microsoft Minecraft, and multiple VMware products, were affected by this vulnerability. Given the widespread use of Log4j in the industry, cybersecurity firms and vendors promptly released software patches to mitigate this vulnerability.
In response to the Log4j vulnerability, organizations have invested considerable time in assessing their environments, identifying vulnerable systems, and mitigating risks. Non-business-critical public-facing systems have been taken offline as a precautionary measure to prevent exploitation. Despite the release of security updates by most vendors, there are still thousands of systems worldwide that remain vulnerable to Log4j attacks.
Ongoing risk mitigation strategies and cybersecurity monitoring are crucial to safeguard against the Log4j exploit. Continuously updating software applications with the latest patches is imperative to ensure the security and integrity of systems. Organizations must invest in robust cybersecurity measures and remain vigilant in detecting and responding to any potential exploitation attempts.
FAQ
What is Log4j?
Log4j is an open-source logging framework maintained by Apache. It is widely used in Java-based systems and applications to log messages and communicate with other services on a system.
What is the Log4j vulnerability?
The Log4j vulnerability refers to a serious zero-day vulnerability discovered in December 2021. It is a vulnerability in the Log4j framework that allows attackers to inject malicious code into the logs, potentially leading to successful denial-of-service attacks.
Why is the Log4j vulnerability a major concern?
The Log4j vulnerability is a major concern because of its widespread impact. It affects a high number of systems and software applications, making them at risk of exploitation due to the lack of a security fix or patch.
How does the Log4j exploit work?
The Log4j exploit works by leveraging the communication functionality of the framework to inject malicious code into the logs. Attackers can then execute this code on the system, leading to various types of attacks and potential control of the remote system.
What is the impact of the Log4j vulnerability?
The Log4j vulnerability had a significant impact on systems worldwide. It resulted in millions of exploit attempts and successful denial-of-service attacks. Various widely used software applications, including Apache Struts, Apache Solr, Apple iCloud services, Microsoft Minecraft, and multiple VMware products, were affected.
How can the Log4j vulnerability be mitigated?
To mitigate the Log4j vulnerability, it is crucial to apply software patches and updates released by vendors. Ongoing risk mitigation and cybersecurity monitoring are also vital to protect against potential exploit attempts.